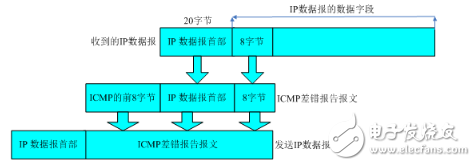
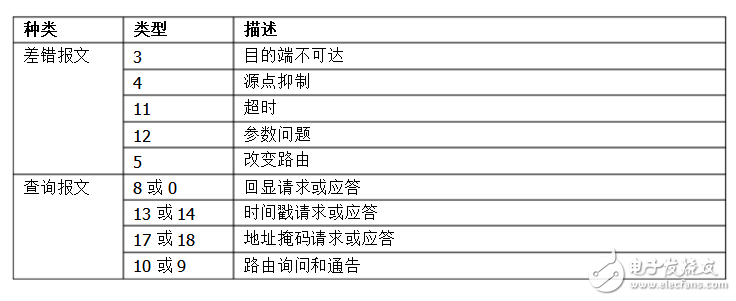
1. ICMP allows hosts or routes to report error conditions and provide exceptions. ICMP is the standard protocol for the Internet, but ICMP is not a high-level protocol, but an IP-layer protocol. Usually ICMP messages are used by the IP layer or higher layer protocols (TCP or UDP). Some ICMP messages return error messages to the user process. 2. The ICMP message is used as the data of the IP layer datagram, plus the header of the datagram, and the datagram is sent out. 3. There are two types of ICMP packets, namely ICMP error report messages and ICMP query messages. The first 4 bytes of all IC MP messages are the same, but the remaining bytes are different from each other. . The type field can have 15 different values ​​to describe a particular type of ICMP message. Some ICMP messages also use the value of the code field to further describe the different conditions. Indicates the data structure of the ICMP header Typedefstruct icmp_hdr { unsigned char icmp_type; //message type Unsigned char icmp_code; //code Unsigned short icmp_checksum; //checksum Unsigned short icmp_id; //ID number Unsigned short icmp_sequence; //serial number Unsigned long icmp_TImestamp; //timestamp } ICMP_HDR, *PICMP_HDR; The various types of ICMP messages are shown in the figure, and the different types are determined jointly by the type field and the code field in the message. The last two lists in the figure indicate whether the ICMP message is a query message or an error message. Because ICMP error messages sometimes require special handling, we need to distinguish them. For example, when responding to an ICMP error message, another ICMP error message will never be generated (if there is no such restriction rule, an error may be encountered to generate another error, and the error generates an error again. Will cycle endlessly). When sending an ICMP error message, the message always contains the first 8 bytes of the IP header and the IP datagram that generated the ICMP error message. In this way, the module receiving the ICMP error message will associate it with a specific protocol (based on the protocol field in the IP datagram header) and the user process (based on the TCP included in the first 8 bytes of the IP datagram). Or the TCP or UDP port number in the header of the UDP packet to judge). 6 . Section 5 will give an example to illustrate. The following conditions will not result in an ICMP error message: 1) ICMP error message (however, ICMP query message may generate ICMP error message). 2) The destination address is an IP datagram of a broadcast address or a multicast address. 3) Datagrams broadcast as link layers. 4) Not the first piece of IP fragmentation. 5) The source address is not a single host's datagram. That is to say, the source address cannot be a zero address, a loopback address, or a broadcast place. Address or multicast address. These rules are intended to prevent broadcast storms that in the past allowed ICMP error messages to respond to broadcast packets. Here are a few common ICMP messages: The ping that we use most daily is the response request (Type=8) and the response (Type=0). One host sends a Type=8 ICMP message to a node. If there is no abnormality on the way (for example, it is discarded by the router, the target If the switch does not respond to ICMP or the transmission fails, the target returns an ICMP packet with Type=0, indicating that the host exists. The more detailed tracert determines the network distance between the host and the target by calculating the node through which the ICMP packet passes. The format of the three types of messages is the same. The target unreachable message (Type=3) is used when the router or the host cannot transmit the datagram. For example, if we want to connect to a non-existent system port (the port number is less than 1024), Will return Type=3, Code=3 ICMP message, it tells us: "Hey, don't connect, I am not at home!", common unreachable types and network unreachable (Code=0), host Unreachable (Code=1), protocol unreachable (Code=2), etc. Source suppression acts as a control traffic. It notifies the host to reduce the data traffic. Since ICMP does not recover the transmitted packets, the host will gradually resume the transmission rate as long as the packet is stopped. Finally, the problem with the connectionless network is that the datagram will be lost, or the network will be roamed for a long time and the target cannot be found, or the congestion will cause the host to reassemble the datagram segment within the specified time. At this time, the ICMP timeout packet will be triggered. The production. The code field of the timeout message has two values: Code=0 indicates the transmission timeout, and Code=1 indicates the reassembly segment timeout. The timestamp request message (Type=13) and the timestamp response message (Type=14) are used to test the transmission time of the datagram between the two hosts. During transmission, the host fills in the original timestamp. After receiving the request, the receiver fills the receiving timestamp and returns it in the format of Type=14. The sender calculates this time difference. Some systems do not respond to such messages. The types of diagnostic packets provided by the ICMP protocol are shown in Table 1.
Put the credit card , some small charge and Coin , it will save your space.Many card slots will give your enough capacity .We sell slim Card Wallet,business Card Holder ,Credit Card Holder,RfID ID card holder,wallet card holder,etc.
We employ the most creative designers and tech brilliant engineers to make the best cases. We believe our high-quality products with competitive prices will satisfy your needs.
The productive process :
Make the Products Mould –Cutting the fabric –Do the half products – Finish products – Cleaning –QC- Package – Shippment .
Rfid Id Card Holder,Id Credit Card Holder,Real Leather Credit Card Holder,Custom Color Credit Card Holder Ysure Leather case 24/7 Support : 86 13430343455 , https://www.ysurecase.com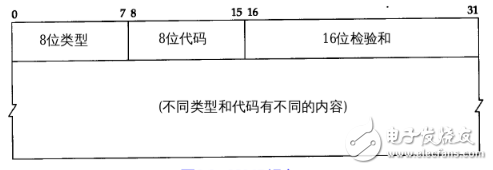




Icmp packet and ip packet analysis
Overview: